Another significant WordPress brute-force attack in the works
So today I’ve experienced a more significant than usual attack against WordPress installations hosted on one of our company servers. So far I’ve blocked more than 17000 21000 unique IP addresses, but the attackers seem to have an endless supply and they’re not slowing down. Note: This article was updated on January 27, 2018.
Thankfully the bots are polite enough to uniquely identify themselves so I’m able to block them on sight without wasting precious server resources by serving their requests.
Every request from this botnet follows the same pattern and provides the same user agent string:
217.101.244.71 - - [25/Jan/2018:20:50:55 +0100] "POST /xmlrpc.php HTTP/1.1" 403 2936 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1" 217.101.244.71 - - [25/Jan/2018:20:50:55 +0100] "GET /wp-login.php HTTP/1.1" 403 2936 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1" 217.101.244.71 - - [25/Jan/2018:20:50:56 +0100] "POST /wp-login.php HTTP/1.1" 403 2936 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1" 217.101.244.71 - - [25/Jan/2018:20:50:56 +0100] "GET /wp-login.php HTTP/1.1" 403 2936 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1" 217.101.244.71 - - [25/Jan/2018:20:50:56 +0100] "POST /wp-login.php HTTP/1.1" 403 2936 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1"
Identify and block the bots
All that’s needed to block this crap is to add Firefox/40.1 to our list of blocked user agent strings:
# BLOCK BAD USER AGENTS
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTP_USER_AGENT} ^.*(jorgee|morfeus|firefox\/40.1).* [NC]
RewriteRule ^(.*)$ - [L,R=403]
</IfModule>
I prefer to use Fail2ban to immediately add these unwanted visitor IP’s to the firewall when they show up in the logs. That way, we’ll save server resources and hopefully keep our customers happy. As an example, the screenshot below shows the jail for IP’s that have abused xmlrpc.php.
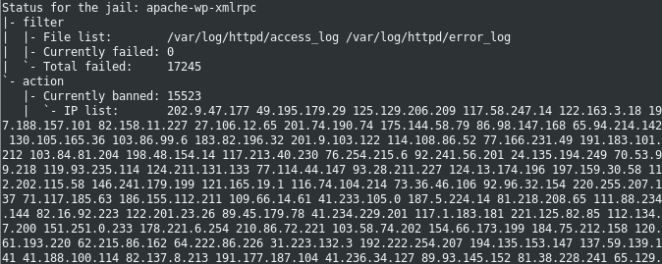
Mr. bot: Go directly to Jail without collecting user credentials.
Origins
According to my data, the IP addresses are originating from 193 different countries. I’ve not had the time to investigate in depth, but it seems the infected clients consists of IoT devices, cloud services and DHT nodes. 11% of the traffic originates from India, but they are far from alone as the number of originating countries suggest.
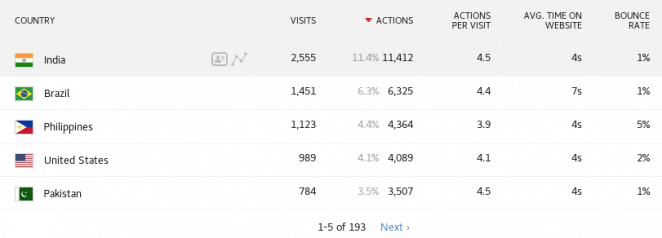
Almost 30% of the traffic originates from these countries.
IP addresses
The attack is still going strong, but I’ve uploaded the 17K 21K of bots that I’ve collected so far to the following repository.
Update- January 27, 2018
So the attackers eventually either ran out of bots or pulled the plug. The attack started at 25/Jan/2018:03:48:30 +0100 and drizzled out at 26/Jan/2018:04:04:03 +0100. During the attack, the botnet made 100178 requests originating from 21490 unique IP addresses. Impressively enough, 193 countries supplied this botnet with ammunition.
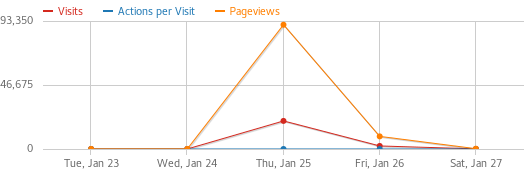
Visitors with the user agent string “Firefox/40.1” over time.
Have a nice weekend, and remember: PATCH /your-software/and-have-a-great-2018/from-the-folks-at-34c3 ;-)