Dictionary attacks against IMAP servers are great again
After the GhostProject started offering access to 1.4 billion credentials in the form of usernames with clear text passwords, I’ve seen an expected increase in attacks against customers e-mail accounts.
For a measly 1€, 1.4 billion credentials could be yours. Donate today using PayPal!
The attacking botnet is using a method often referred to as the “drip” approach. In short, that technique involves attempting only a few logins per minute while each individual bot gets a long grace period between attempts. This is a highly effective approach to avoid triggering monitoring software and automated IP block services like Fail2ban.
Anyhow, as I was already familiar with the database of credentials that the GhostProject is selling, I knew in advance which accounts and domains were likely to be attacked. During the week, one email server hosting a few enticing domains had just short of 40 000 failed login attempts, courtesy of a botnet deploying around 8 000 zombies.
Not much to write home about really, but the email server in question has a few region blocks (such as China), which probably turned away a substantial number of attacks.
I always find it interesting to determine where the bots are coming from geographically, and what kind of comprised equipment they’re running. After examining the data, the top five originating countries accounted for nearly 50% of the attacks.
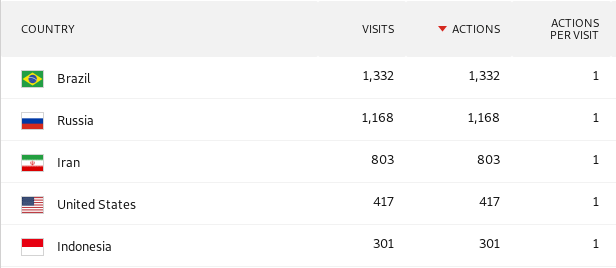
Top five attacking countries: Brazil, Russia, Iran, USA and Indonesia.
And what kind of equipment powered this botnet? Well, no surprise there, it consisted mainly of compromised MikroTik routers. How disappointing, I thought that garbage was busy with cryptomining.
The list of offending IP addresses are available from this repository.