Gentoo - Tor 0.3.4.9 stable on amd64
So why is this release noteworthy? Well, I experienced an issue with the previous release (Tor 0.3.4.7) where I was unable to get sandboxing to work due to the following error:
(Sandbox) Caught a bad syscall attempt (syscall openat) ...
At the time, I really wanted to launch my v3 onion so I decided to just run Tor without sandboxing, instead of rolling back to an earlier release.
I’ve since become aware that this particular issue might have been caused by a change in glibc where the open() wrapper was changed to call openat(), which could potentially break seccomp() filters.
*Don’t quote me on that though, it’s way above my paygrade ;-)
Anyhow, this server is now running glibc 2.27 and Tor 0.3.4.9 on Gentoo Linux and Tor sandboxing is again working as advertised.
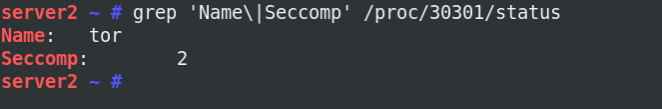
Showing the seccomp flag from the Tor process (2: Seccomp-bpf is enabled ).