Self-hosting email in 2020 – Joe Nobody vs. World
I recently moved my self-hosted email service from Scaleway to DigitalOcean. After receiving a new IP address for my mail server, I’m effectively once again the new kid on the block. Let’s find out if the big kids are willing to talk with me if I play nice and put on my best behavior.
Additionally, I have 15 years of professional experience with delivering, hosting and maintaining mail servers so what could go wrong?
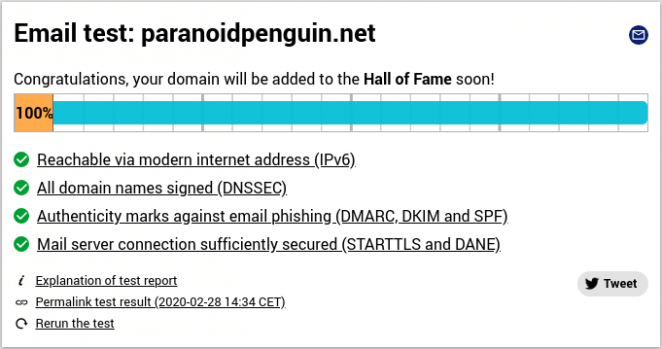
Testing the implementation of modern Internet standards by courtesy of internet.nl
Anyhow, let’s rewind a bit and go over a few bullet points I believe are worth considering before establishing your self-hosted email service.
Choosing the right Top Level Domain
Several of the new gTLDs (generic top-level domains) are predominately used for spam and other malicious activity. Keep that in mind when deciding under which TLD to buy a domain name:
- Prefer an established gTLD (.com/.net/.org) or a ccTLD (country code top-level domain).
- The TLD must support DNSSEC.
- The DNS provider must support TLSA records (used for DANE).
Implementing DANE is only possible for DNSSEC enabled domains.
Choosing a cloud infrastructure provider
Not all cloud providers are created equal. When hosting a mail server you should find a provider that at least has a policy against unsolicited email:
- Choose a provider with a decent ASN (Autonomous System Number) reputation.
- The provider must offer both IPv4 and IPv6 networking.
- The provider must allow custom reverse DNS for both IPv4 and IPv6.
- The provider must allow outbound traffic on port 25.
Many cloud providers will demand some kind of identification on your part to be allowed outbound traffic on port 25.
Configuring your mail server
Configure your email service according to best security practices:
- Make sure the IP address provided to your instance is not already listed in any DNS based email blacklists.
- Configure reverse DNS for your IPv4 and IPv6 addresses.
- Implement and configure SPF, DKIM and DMARC.
- Implement and configure StartTLS and DANE.
- Block unauthenticated relay of emails.
- Always keep your software stack up to date.
Managing SPF, DKIM, DMARC and DANE records for paranoidpenguin.net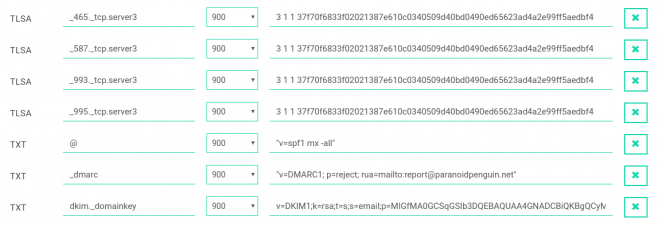
Verifying your mail server configuration
Before we start delivering out email and open the floodgates, let’s make sure that everything is configured correctly. I’m using Internet.nl and SSL-Tools to verify the configuration and technical capabilities of my mail server.
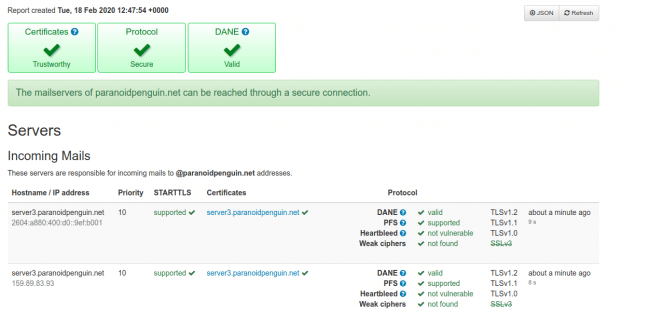
The result from running the encryption test provided by ssl-tools.net on my mail server.
To get an opinion on the spammyness (as they put it) of my emails, I’m using the free service from mail-tester.
And now, email delivery
Finally, I’ve taken every precaution to authorize, authenticate, sign, encrypt and secure everything, everywhere. I’m now ready to harvest the fruits of my labor and enjoy my new and reliable email service. Surely, no external mail service would ever label my emails as spam, unless you know… they were actually spam.
Anyhow, I’ll put this questionable theory to the test by emailing everyone’s favorite email services to find out if my message ends up in the intended recipient’s inbox.
To make this test more reliable in terms of how my emails are treated by the external email service, I’ll do the following:
- Create a new recipient email account with the external email service to avoid any previous communication influencing the result.
- Create a new sender email account on my own service to avoid any previous communication influencing the result.
Outlook.com
The first provider on my list was Microsoft and their free outlook.com email service. But wait, what happened? The message was delivered directly to the recipient’s spam folder and scheduled for automatic deletion in ten days. Microsoft is feeling confident that all my emails are spam.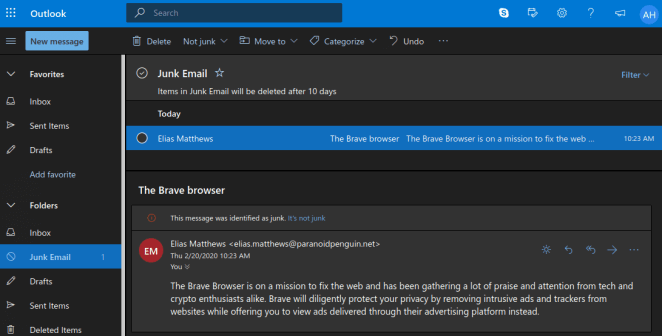
Gmail.com
Ok, so we’re off to a bad start but who’s using outlook.com anyway? Surely I’ll perform better with Google’s popular Gmail service. Fingers crossed. Google is in full agreement with Microsoft. All my emails are spam.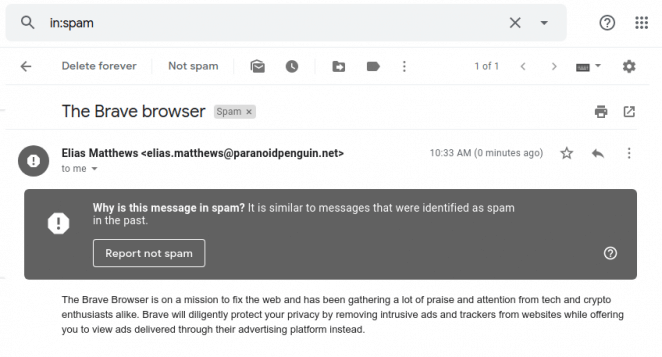
Icloud.com
I guess I have to turn to Apple for some fair and unbiased treatment. Wrong again, Apple’s email servers won’t even talk with me: Darn you Tim Apple! I’m never buying another iPad.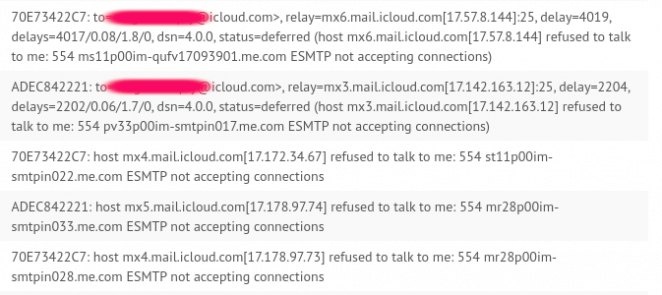
Zohomail.com
Zohomail.com classified all my emails as spam.
Yahoo.com
For some reason Yahoo still provides a free email service. My message was delivered straight to the recipient’s inbox without issues. Even so, I would not recommend getting an email account with Yahoo.
ProtonMail.com
ProtonMail rivals the technical excellence of my own mail server. Naturally, my message was delivered straight to the recipient’s inbox without issues.
Tutanota.com
Like ProtonMail, Tutanota rivals the technical excellence of my own mail server. Naturally, my message was delivered straight to the recipient’s inbox without issues.
End of part one
The result was mostly as expected, but there were a couple of surprises. Yahoo Mail delivering my message directly to the recipient’s inbox was one. In contrast, Apple was outright blocking my mail server without providing any additional information.
Seeing how Microsoft and Google are advocating the use of SPF, DKIM and DMARC to battle spam, one might be enticed to believe that adding support for these technologies would increase the chances of bypassing their spamfilters.
In the upcoming conclusion, we’ll “expose” the real reason behind why Microsoft, Google and others are classifying my emails as spam.