How to back up your 2FA secret keys with KeePassXC
The amount of services offering (or even demanding) two-factor authentication (2FA) is ever-increasing. This has encouraged me to find a more resilient strategy for how I store, manage, and backup my secret keys. My old approach relied solely on using time-based one-time password (TOTP) applications capable of exporting and importing 2FA accounts.
The limitations of this strategy became painfully evident when I wanted to use a TOTP authenticator on my iPad. Unsurprisingly, the TOTP application I was using on Android was not available for iOS, and thus my export and import strategy failed at the very first hurdle.
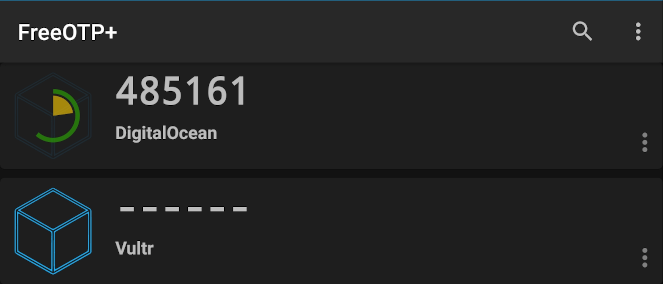
FreeOTP+ on Android. An open-source TOTP authenticator with backup capabilities.
After exporting 26 2FA accounts in clear-text and painstakingly adding them one-by-one with the TOTP authenticator on the iPad, I concluded that the ability to export and import 2FA accounts wasn’t the be-all and end-all solution I expected it to be.
Why KeePassXC?
Simply put, I want an open-source cross-platform password manager for the desktop, capable of handling TOTP. It will function as my primary backup and safe storage while allowing me to configure additional mobile authenticators on the fly. No more returning to work after hours to pick up the cell phone I left behind with my only authenticator.
Show me the keys
When configuring two-factor authentication for a service, you’ll receive a shared secret key to configure your TOTP authenticator. Granted, this is usually provided in the shape of a QR code that your authenticator scans and subsequently use to set up the account.
The QR code is just a specially crafted URI containing the secret key, issuer, label, and algorithm. The majority of 2FA capable services nowadays provide you with the secret key during configuration, but in case they don’t, any QR code scanner may be used to retrieve the required information.
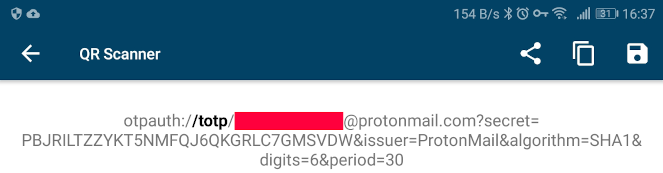
A look at the actual content of a QR code showing the secret key needed for TOTP.
Setting up TOTP with KeePassXC
I’ll create a separate KeePassXC database for my 2FA accounts as I don’t want to store them together with the actual account credentials (you could though) for which they provide 2FA. KeePassXC will give me a fallback option when I don’t have access to my mobile authenticator. Additionally, it will come in handy every time I need to install an authenticator for a new device.
Anyhow, the first step is to add a new entry to the database and then right-click it to select TOTP => Set up TOTP.
Paste in the secret key you previously extracted and click OK. When you right-click the entry once more and select TOTP, you’ll have a few additional options:
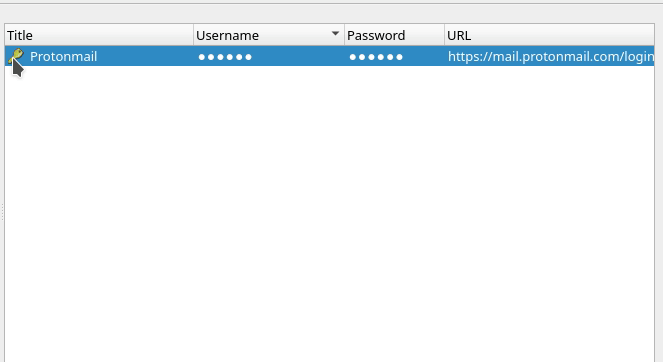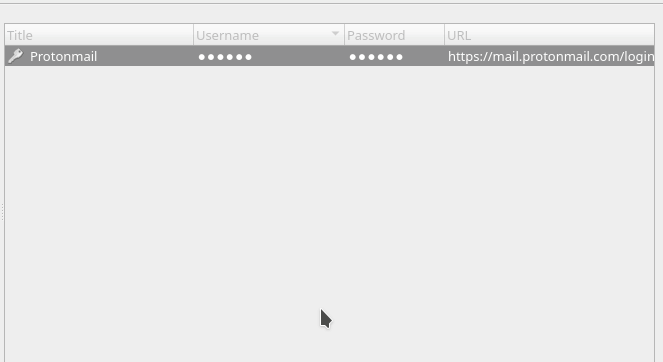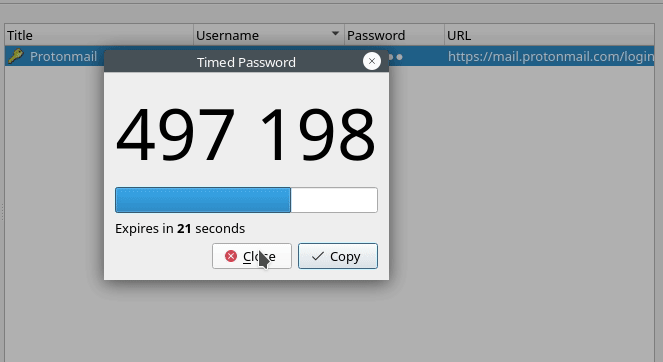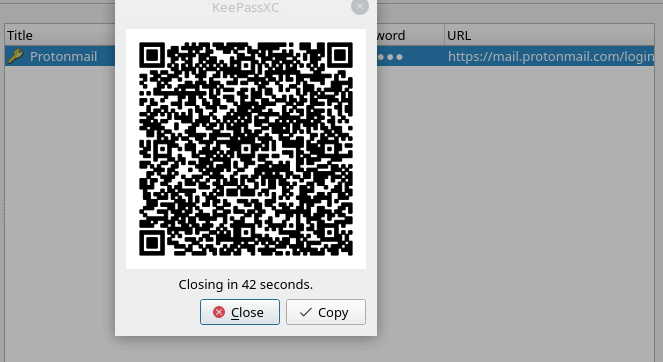
- Copy TOTP: Copy the time-based one-time password for authentication.
- Show TOTP: Show the time-based one-time password for authentication.
- Show TOTP QR Code: Generate a QR code that you can scan and import with your favorite mobile TOTP authenticator. The entry title will be used for the issuer, and if you provided a username it will be used for the label.
- Set up TOTP: Show the secret key used for the account.
The dark side clouds everything
With this configuration, there is no need to rely on any proprietary software or services. I don’t have any interest in cloud synchronization and backup in exchange for vendor lock-in and total lack of privacy.
Free open source authenticators:
- KeePassXC is cross-platform password manager.
- andOTP is a two-factor authentication App for Android*
- FreeOTP Plus is a two-factor authentication App for Android*
- iOS Authenticator is a two-factor authentication App for iOS.
- Windows Authenticator is a two-factor authentication App for Windows.
*= Get it on F-Droid.