Sex, drugs and no-reply@sharepointonline.com
Is there anything more annoying in this world than dealing with Microsoft support? You might assume that Microsoft would appreciate reports detailing the abuse of its services or even act upon that information. But alas, in both cases you’d be wrong.
Content warning: This article contains mildly sexually explicit text and images.
One of the more annoying spam campaigns of the year has been the endless stream of sex adverts delivered from no-reply@sharepointonline.com, caused by potentially compromised Office 365 tenants.
Spam as a service
The culprit (manually or scripted) uploads a file to Sharepoint Online, adds a clickbait title, and feeds Microsoft a list of desired targets (recipients). Microsoft will then diligently email all victims to inform them that they have received a shared document.
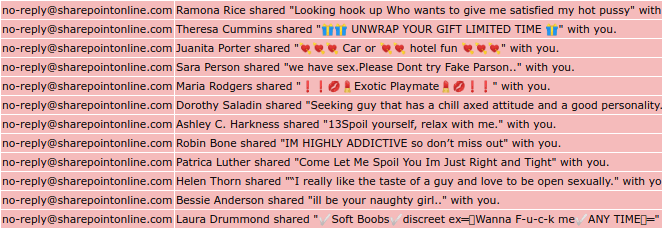
A list of spam messages received from no-reply@sharepointonline.com.
With the added benefit of having the spam created on, and delivered entirely through Microsoft’s infrastructure, it successfully clears any SPF and DKIM checks on their travel to the target’s mailbox. Microsoft’s own spam filter confidently classifies these messages as NSPM (non-spam).
I am unsure as to why no-reply@sharepointonline.com is configured as the sender address. The address was previously shared by all Office 365 tenants for various email communication scenarios, but the service was discontinued back in November 2019.
In that regard, an interesting detail I found by examining the email headers was that the value of the X-OriginatorOrg header field would always reference an onmicrosoft.com subdomain instead of a verified domain name.
From Russia with love
Once the message reaches the intended recipient’s mailbox, it’s apparent why spam filters have a hard time identifying the message as spam. Besides the document title, there is not much to work with as the document links to a trusted source, namely sharepoint.com.
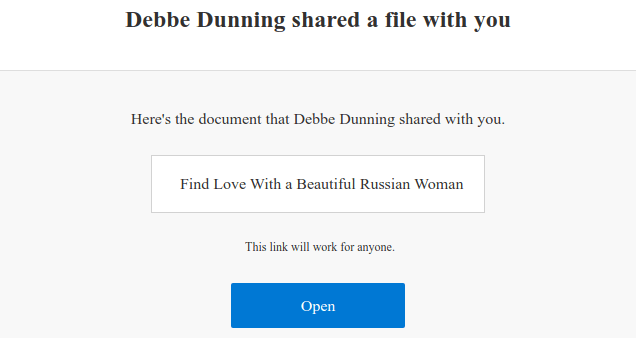
Is that a gun in your pocket?
Should the recipients be silly (or lonely) enough to open the linked document, they’ll receive an invitation to a dating or escort service. Though I have serious doubt about the effectiveness of these ads, I guess the spammers are hoping for some added legitimacy and protection by using Microsoft’s enterprise platform for delivery.
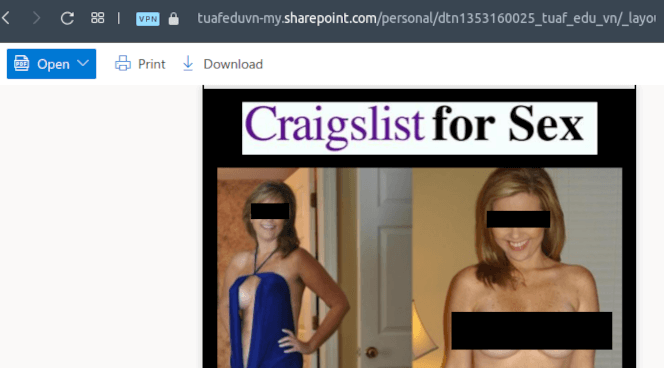
X-OriginatorOrg to judge them all
After scraping the earlier mentioned X-OriginatorOrg header fields from the spam messages, a clear pattern emerged. Only a few Office 365 tenants were responsible for the entirety of the bulk spam delivered to our inbound mail servers.
Not discouraged by previous setbacks with Microsoft support, I decided to fill out an abuse report and share the data I had collected. After all, it should be in Microsoft’s best interest to strike down on this behavior.
Three wise monkeys
Well, I had this one figured all wrong. Microsoft is not responsible for any abuse on their platform, their customers are. And what’s more, it’s none of my business.
The activity reported is associated with a customer account within the Microsoft Azure service. Microsoft Azure provides a cloud computing platform in which customers can deploy their own software applications. Customers, not Microsoft, control what applications are deployed on their account.
The specific details of this case will not be provided in accordance with our customer privacy policy.
Thank you,
Computer Emergency Response Team
That is not even a reply but merely the content of a standard response template. After all, there is no reason to play by the book when you already own the game.