Unexpected VPN bypass attempts on Arch Linux
So I was minding my own business while connected to my VPN service when I noticed several blocked outbound network connections appearing in my firewall log. For some reason my wifi adapter (wlp3s0) was trying to connect directly to the internet without having traffic routed through my VPN interface (tun0). Was this my reward for not reviewing AUR PKGBUILD files, or was there another explanation as to why wlp3s0 wanted to disclose my real IP address?
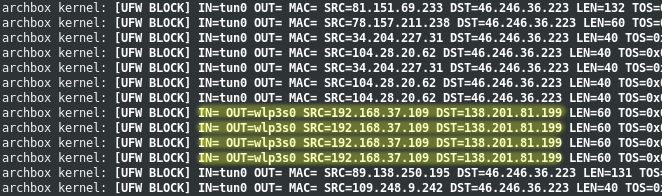
UFW blocking outbound connections from wlp3s0 to deny an identity exposure.
From the connection attempt, we notice that the wlp3s0 interface is trying to connect to the IP address 138.201.81.199 on port 80 (HTTP). A reverse DNS lookup on 138.201.81.199 resolves to the host apollo.archlinux.org.
There is no configured site on apollo.archlinux.org but it provides a (broken due to HSTS) 301 redirect to www.archlinux.org.
$ curl -Ik https://apollo.archlinux.org HTTP/2 301 location: https://www.archlinux.org/ strict-transport-security: max-age=31536000; includeSubdomains; preload $ host www.archlinux.org www.archlinux.org is an alias for apollo.archlinux.org. apollo.archlinux.org has address 138.201.81.199 apollo.archlinux.org has IPv6 address 2a01:4f8:172:1d86::1
Ok, atleast the traffic is most likely not originating from some malicious program I installed.
The culprit
NetworkManager, which by the way does not manage my VPN connection, has an optional connectivity checking feature to determine if the system has internet access. This check is performed periodically by connecting to a predetermined web page (enter 138.201.81.199).
On Arch Linux, the configuration is done from /usr/lib/NetworkManager/conf.d/20-connectivity.conf:
[connectivity] uri=http://www.archlinux.org/check_network_status.txt
The check_network_status.txt file is only available over plain HTTP and thus broken by design when implementing strict-transport-security (HSTS) for archlinux.org including all subdomains. Arch developers obviously care about HTTPS so why not support encrypted connections for this feature?
The solution
Anyhow, to disable the connectivity check, it’s enough to simply set the interval to zero (if missing, the default is 300 seconds).
[connectivity] uri=http://www.archlinux.org/check_network_status.txt interval=0
Finally, issue the systemctl restart NetworkManager.service command to activate the new configuration.
I don’t personally care much for this NetworkManager feature or how it’s implemented on Arch Linux but I understand that other people might find it useful. However, I would strongly recommend to always block outbound connections from other network interfaces when using VPN, if you value your privacy that is.
Source: man NetworkManager.conf