Did Microsoft just roll out MTA-STS and TLS-RPT?
A few months ago I was complaining about the lack of MTA-STS adaptation with major email service providers besides Google. Recently though, I’ve noticed a new player connecting to mta-sts.paranoidpenguin.net to retrieve my MTA-STS policy.
Nginx excerpt:
mta-sts.paranoidpenguin.net:443 2a01:111:f400:fe06::100 - - [26/Aug/2020:08:19:51 +0000] "GET /.well-known/mta-sts.txt HTTP/1.1" 200 103 "-" "-"
mta-sts.paranoidpenguin.net:443 2a01:111:f400:fe06::100 - - [26/Aug/2020:08:29:07 +0000] "GET /.well-known/mta-sts.txt HTTP/1.1" 200 103 "-" "-"
mta-sts.paranoidpenguin.net:443 209.85.238.243 - - [26/Aug/2020:10:27:00 +0000] "GET /.well-known/mta-sts.txt HTTP/1.1" 200 110 "-" "Google-SMTP-STS"
mta-sts.paranoidpenguin.net:443 209.85.238.245 - - [26/Aug/2020:22:27:01 +0000] "GET /.well-known/mta-sts.txt HTTP/1.1" 200 110 "-" "Google-SMTP-STS"
The IPv6 address of 2a01:111:f400:7d00::100 does indeed belong to Microsoft. That server pulls the policy on behalf of Microsoft 365 (formerly known as Office 365) and outlook.com. As for the icing on the cake, I just received my first ever email from tlsrpt-noreply@microsoft[.]com, containing an aggregate TLS report:
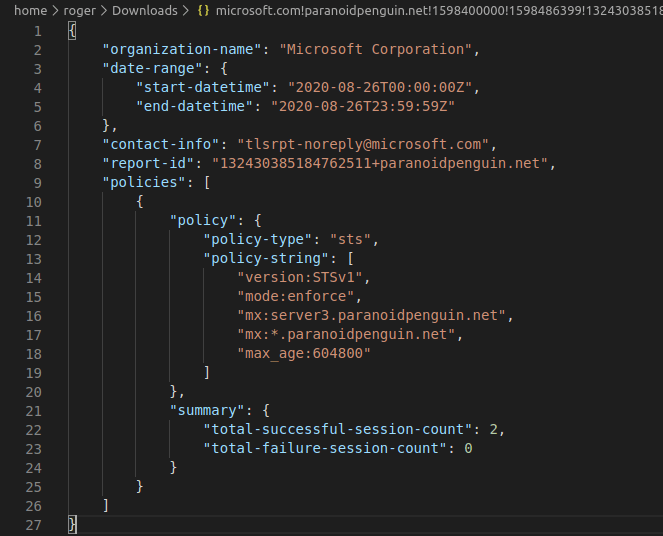
Behold, an aggregate TLS report from microsoft.com.
So will mandatory authentication checks and encryption grant my mail server a favorable reputation when communicating with Microsoft’s email services? Honestly, I’m not holding my breath. However, seeing how Google and Microsoft are now both supporting MTA-STS and TLS-RPT, I believe it’s worth implementing the mechanism for your own email services.
Addendum
The MTA-STS policy for outlook.com is still in testing mode:
version: STSv1
mode: testing
mx: *.olc.protection.outlook.com
max_age: 604800